A security operations centre (SOC) is a hub managed by a security team to continuously monitor and analyse an organisation’s cyber security posture. Using a combination of processes and technologies, a SOC team can quickly prevent and respond to cyber security incidents.
Over the past three years, the number of cyber security incidents has increased exponentially due to a growing reliance on technology for business-critical operations. According to IBM, the UK experienced the highest number of cyberattacks among European countries in 2022, accounting for 43% of incidents.
This is why a SOC is so important to an organisation’s safety. In this insight, we provide an overview of SOC processes and components, as well as the benefits and challenges of implementing one.

Overview of a SOC
The main function of a SOC is to prevent, detect, analyse, and respond to cyber security incidents in real-time to limit financial, operational and reputational damage. In order to work effectively, a SOC needs to be run according to a strategy which considers wider business goals as well as existing infrastructure.
This helps the team monitor and protect data while staying compliant with industry standards and government regulations. The next section details specific processes and technologies which constitute a good SOC.
SOC processes and technologies
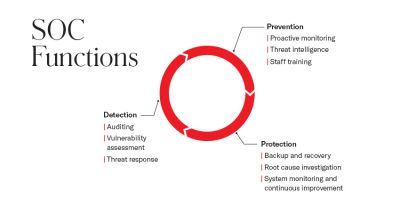
A SOC’s responsibilities can be grouped into three different categories: prevention, protection and detection. Within each category, processes are put in place to facilitate threat intelligence, vulnerability assessment and systems monitoring. Key processes include:

Asset discovery and management
The SOC provides a complete overview of an organisation’s infrastructure, including on-premise endpoints, software and servers, as well as cloud services and website traffic. This also includes preventive maintenance, which ensures all assets are always working properly and updated regularly.
Proactive monitoring
In order to be considered proactive, system monitoring needs to happen 24/7, 365 days a year. Proactive behavioural monitoring enables the team to instantly detect anomalies and focus equally on proactive and reactive measures. Systems can be accurately monitored through predictive automation, where data is collected and used to train the SOC to predict malicious activity and adjust the information if false positives occur.
Security information and event management (SIEM) platforms are most commonly utilised for this purpose. A SIEM platform is a vital component of a SOC as it aggregates data from multiple sources, identifying anomalies and taking instant action.
Advanced SIEM platforms now include user and entity behaviour analytics (UEBA) and security orchestration, automation and response (SOAR). These technologies give organisations an overview of all security data from a single source, making it easier to identify unusual patterns in time.
Alert management
SOC teams have to handle high numbers of alerts. Alert severity ranking ensures that the most urgent issues are resolved first, thus limiting damage.
Activity logs
All communications and activities happening across an organisation are logged by the SOC. When a cyber incident happens, the team can check the log and trace back to any action that might have led to the incident.

Threat response
When an incident is confirmed, the SOC performs all the necessary actions for mitigation. This can include isolating affected endpoints, preventing harmful processes from executing or terminating existing ones, and deleting files. Threat response has to be as quick and smooth as possible in order not to impact business operations.
Recovery and root cause investigation
After an incident, the SOC restores all assets by restarting systems and recovering data using existing backups. This process aims to restore the organisation’s network and infrastructure to its state before the incident. It then uses past data logs and information about what happened during the attack to investigate the root cause and prevent similar issues from occurring in the future.
Continuous improvement
As hackers are constantly finding new ways to steal data, the SOC is responsible for keeping devices and software up to date. Teams make sure to always adhere to the company’s cyber security strategy and update it when needed.
Benefits of implementing a SOC
A SOC is essential to keep your organisation safe in the digital age. As well as keeping all your data safe and reducing potential downtime from cyberattacks, here are a few benefits of implementation:
- Uninterrupted monitoring for suspicious activity
- Improved incident detection and response times
- Reduced financial losses associated with data breaches and other cyber security incidents
- Improved customer satisfaction
- Increased transparency and compliance
- Better control over company data
- Increased operational efficiency
Challenges of implementing a SOC
While having a SOC offers many benefits, organisations still encounter many challenges during the implementation process. In order to implement effectively, businesses may have to overcome three main challenges:
Talent and skill shortages
Staff shortages are a long-standing issue in the IT sector. If an organisation is unable to hire trained staff, existing employees will have to fill the skill gap. This is likely to result in a higher number of mistakes and missed attacks, as the fast-changing threat landscape becomes increasingly challenging to navigate.
Relying on an IT managed services provider that has an established SOC service can solve this issue, enabling access to specialised talent.
Legacy tools
Lack of appropriate security tools is a common issue for businesses, especially those shifting from an on-premise to a cloud environment. Upgrading cyber security is key when upgrading the entire infrastructure and moving to a new environment.
Disconnected systems
Lastly, a lack of system integration makes it impossible to develop an effective SOC. The inability to gather data from a single source can create alert fatigue and false positives, making it difficult to spot threats in time and increasing the chances of human error. Similarly, disconnected systems hinder process automation, which is essential in SOCs handling large numbers of alerts.

How to build a SOC
Building a SOC is a rigorous process that must consider organisational goals and resources and start from a well-defined cyber security strategy. Here are three steps ROCK follows to build an effective SOC:
Develop a SOC strategy
The first step is to define the scope of your SOC based on your organisation’s security requirements and current gaps. Your SOC strategy should also include regular blue-team and red-team[AM2] exercises, testing your SOC’s ability to detect and effectively neutralise threats as quickly as possible. In these exercises, the red team plays the role of the attacker trying to penetrate the system, while the blue team responds with protective measures.
Define the SOC team structure
Next, you should define your SOC team’s structure. The team determines how successful your organisation will be in responding to an attack or breach, so it is important that roles are defined clearly from the start. A great SOC team should include:
- An incident responder, who monitors security tools, identifies and prioritises threats.
- A security investigator, who identifies affected devices, performs threat analysis and implements a mitigation strategy.
- An advanced security analyst, who identifies new vulnerabilities, reviews past activity logs and recommends security products.
- A SOC manager, who manages the entire team and communicates with business leaders and stakeholders.
It is important to note that a SOC team needs to be big enough to guarantee 24/7 coverage as well as staff turnover, sickness and absences. This is why relying on a managed IT services provider with an established SOC is generally your best bet.

Select the right technologies
As well as selecting the right SIEM and SOAR tools, you should implement technologies to cover the following areas:
- DNS security
- Network detection and response
- Data discovery
- Anti-phishing

“As cyber threats continue to evolve, a Security Operations Centre provides critical 24/7 monitoring, detection and response capabilities for our clients’ protection.”
Ian Elsbury, Managing Director at ROCK
Conclusion: protect your assets and create value with a SOC
A SOC is a key asset for enterprises in the digital age allowing security teams to prevent cyber threats and immediately spot an ongoing attack.
However, setting up a SOC is a complex process requiring specialist knowledge. Increasingly, businesses are turning to strategic partners to deliver cyber security services. This results in better system integration, reduces costs and removes the burden of setting up and maintaining from internal IT teams.
At ROCK, our comprehensive cyber security services are tailored to your needs. Our dedicated team of architects, engineers, analysts and developers will implement the right security for your business and assist in creating a SOC. Start the process with a free security audit today.