An information security management system (ISMS) is a framework for managing and protecting integrity, confidentiality and availability of an organisation’s data. It includes policies and processes to protect sensitive information from breaches, unauthorised changes or accidental loss.
An ISMS is regulated by internationally recognised frameworks, some of which are also widely used in IT service management (ITSM). This ensures organisations are fully compliant with data protection laws and standards like the General Data Protection Regulation (GDPR).
This insight explains how an ISMS works, its benefits, and the best implementation practices to protect your organisation’s most sensitive assets.
How does an information security management system work?
An ISMS offers a systematic and holistic approach to information security in a business, including policies to manage security risk levels. ISMS practices are regulated by the ISO/IEC 27001 international framework, which provides recommendations for documentation, preventive action, and continual improvement.
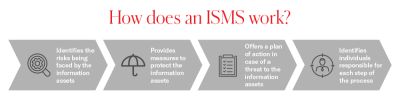
Organisations can become ISO 27001 certified by implementing an ISMS that takes into account the risks faced by the information assets, the steps taken to protect them, a plan of action to tackle a security breach, and the definition of roles within the information security process.
Benefits of an information security management system
An ISMS can be tailored to the specific needs of an organisation and allows for flexible levels of control. For example, in highly regulated sectors such as legal or healthcare, there may be a need for more sophisticated systems to ensure sensitive client data is protected.
Along with flexibility, an ISMS offers many benefits, including:
Enhanced data protection
An ISMS is designed to protect all types of assets, from paper to digital, to on-premise and cloud. Thanks to continuous improvement, an ISMS also helps organisations prepare for new cyber threats and navigate the ever-changing threat landscape.
Regulatory compliance
An ISMS helps organisations keep up with regulatory requirements and relevant laws such as GDPR, protecting critical infrastructure and avoiding fines.
Business continuity
An ISMS drastically improves an organisation’s security posture, reducing the number of security incidents as a result. This means less downtime and less disruption to services, aiding business continuity.
Reduced costs
Increased business continuity also means reduced financial losses from security incidents. Additionally, through a risk assessment, an ISMS enables organisations to identify high-risk assets so they can effectively direct resources where they are needed.
Implementing an information security management system
There are several ways to set up an ISMS. It can be a complex process. Many organisations follow a plan-do-check-act model for continuous improvement but often partnering with an ISO 270001-certified service provider is the best choice.
This section illustrates the factors to consider before investing in an ISMS and how to implement one.
Pre-implementation best practices
The ISO 27001 provides a checklist of things to consider before investing in an ISMS, including:
- Business needs – Understand your business operations, existing information management tools and security requirements.
- Information security policy – An information security policy that provides an overview of security controls can be helpful to identify any weaknesses before setting up an ISMS.
- Data access monitoring – Organisations must ensure that only authorised employees have access to sensitive information, monitoring data access by tracking logins and implementing strict policies.
- Data backup and encryption – All business-critical data should be encrypted and backed up either on-premises or in the cloud.
- Security awareness training – All employees should be regularly trained on vulnerabilities, prevention and mitigation strategies.
- Internal security audit - Internal audits should be performed before executing an ISMS to identify and fix existing vulnerabilities as well as gain an overview of devices and security systems.
5 steps to implementing an ISMS
There are five main steps to implementing an ISMS
- Identify assets and objectives – Consider your business and client's objectives to determine which assets need protection and what you want to achieve with an ISMS.
- Create an inventory – Create an inventory of company hardware, software, services and databases with a business process map.
- Assess the risks – Assess risk factors according to compliance requirements and evaluate which ones are acceptable and which ones need to be avoided at all costs.
- Define mitigation measures – Once you know what the risks are, plan how to mitigate them, including relevant policies and rules.
- Focus on continuous improvement – All measures should be audited and continuously updated to account for new risk factors and emerging threats. Starting the ISMS process from scratch periodically will enable the ISMS to quickly adapt and respond to changing conditions.
Conclusion: protect business-critical assets with an ISMS
An ISMS is a vital tool for organisations wanting to protect business-critical data. As an ISO 27001-certified provider, ROCK helps clients set up an effective ISMS and continually improve it to protect their data. We also offer other essential cyber security capabilities, such as SOC-as-a-service and cyber security analytics.