In recent years, cyber security has become a critical priority for businesses. The increasing reliance on digital technology for day-to-day operations and the rise of remote working have contributed to an uptake in cyberattacks.
From healthcare to finance and the public sector, all industries are affected. According to the most recent UK Government Cyber Security Breaches Survey, 39% of UK organisations in the sample identified a cyberattack between 2021 and 2022. Of these, 35% of businesses and 38% of charities faced at least one negative consequence as a result. That means up to 1.9 million UK businesses and up to 156,000 UK charities could have been negatively affected by a cyberattack last year.
Organisations need to ensure their infrastructure, systems and services are safe from data breaches and information theft – starting with a cyber security risk assessment. A cyber security assessment is vital to identify potential weaknesses and meet compliance requirements with data protection laws such as the General Data Protection Regulation (GDPR) or the UK Data Protection Act.
This insight explains the benefits of a cyber security risk assessment and how to conduct one.

What is a cyber security risk assessment?
A cyber security assessment is a review of an organisation's IT infrastructure conducted by an external or internal team. The audit evaluates existing cyber security protocols and suggests new or improved ones if necessary.
Assessments allow companies to identify potential vulnerabilities in their systems and prevent data breaches, both in terms of devices and internal employee practices. A thorough assessment mitigates the risk of financial loss from data breaches. In 2022, the average cost of data ransomware attacks in the UK was $1.08 million (about £871,000). In the previous year, data breaches cost $4.5 million on average (about £3.7 million).
But financial losses are not the only cause for concern in the aftermath of a cyberattack. Reputational damage can hinder an organisation’s relationship with stakeholders. A cyberattack can also cause disruptions to key services, with potential risk to people’s lives in the case of charities providing meals or other essential goods to vulnerable citizens.
Additionally, a lack of regulatory compliance can result in significant fines, unless there is proof that every possible precaution was taken to prevent the incident. Since the introduction of GDPR in 2018, the UK has issued €44 million (£38.6 million) worth of fines due to insufficient information security measures.
Cyber security risk assessment help ease these concerns. The next section details the essential components and the process of a cyber security risk assessment.
1. Update operating systems
While operating systems can be set to automatically perform core updates, you should always ensure that your infrastructure is running on the latest version of the chosen operating system and that updates are tested.
For example, as Microsoft announced the end of support for Windows 8.1 this month, many organisations will need to upgrade to ensure system security. Failure to update systems can increase the likelihood of cyberattacks.
2. Check access management
Make sure to have a comprehensive view of who has access to your organisation’s systems and implement a protocol for access management and password management. This will limit the scope of a potential data theft incident.
3. Provide employee training
Lack of cyber awareness is the leading cause of preventable cyberattacks. A 2021 survey by TalentLMS surveyed a thousand employees and found that 61% of them could not answer basic cyber security questions.
At ROCK, we often work with clients looking to improve their cyber security posture as a result of employees not changing their passwords for many years and not knowing hackers can encrypt data through phishing links in emails.
Employees should be trained on the risks of opening links and attachment in emails and encouraged to seek advice from the IT team in case of suspicious activity.
4. Review security measures and policies
Protecting your business with layered security solutions is crucial. Make sure to consistently review and update your antivirus software as well as your data loss prevention policies. This is especially important if your business works primarily in the cloud, where document sharing and file encryption might need to be regulated.
5. Back up your data
Alongside reviewing your policies, backing up sensitive business data cannot be overlooked. Storing data in a secure, encrypted and immutable remote location ensures that it stays accessible even in the event of a cyberattack, accidental deletion or natural disasters.
ROCK’s cyber security risk assessment methodology
Assessing your organisation’s cyber security solutions and practices is no easy task. Relying on an IT managed service provider (MSP) to assist can make the process smoother and more cost-effective, ensuring no mistakes are made.

“I highly recommend that businesses consider an impartial third-party organisation such as ROCK to provide validation and security assessments. This mitigates against the possibility of any conflicts of interest, and provides assurances to businesses on their security posture and remediation strategy.”
Tom Derham, Head of Technology at ROCK
At ROCK, we provide a vulnerability assessment including regular reporting on your organisation’s cyber security posture. Using industry-leading cyber security platforms, we evaluate potential threats, both internal and external to the network environment.
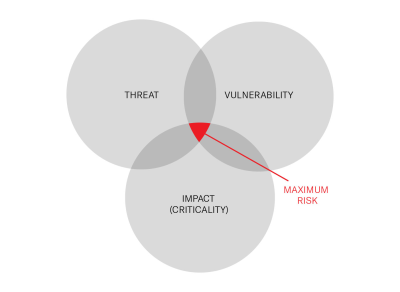
After reviewing the reports, ROCK’s Cyber Security Specialist Consultants will create a Cyber Action Plan with tailored recommendations. By analysing the threat variables, including specific vulnerabilities and potential impact, ROCK will assign a risk score to determine priorities.
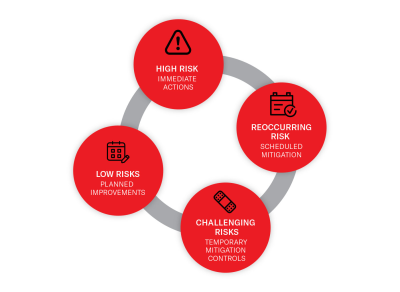
Each issue is categorised using the Common Vulnerability Scoring System (CVSS). The urgency of action and subsequent cyber security roadmap are determined as follows:
- High risk – immediate action
- Recurring risk – scheduled mitigation
- Challenging risks – temporary mitigation controls
- Low risks – planned improvements
We offer three tiers of vulnerability assessments catering to different levels of compliance and typical risk assessment strategies used by our clients:
- Premium security (monthly) – Reduced intervals between scans decrease the time for issue detection and significantly reduces business risks.
- Standard security (quarterly) – Regular scanning to manage the time for issue detection and reduce business risk.
- Health check (one-off/annually) – Appraisal and validation of business security
Conclusion: protect your business with a cyber security risk assessment
Cyber security is a business-critical priority. Failure to adopt appropriate cyber security measures can compromise operational security, resulting in reputational and financial damage. That is why cyber security audits are so important.
Consistently reviewing and updating your organisation’s security policies and IT infrastructure ensures key services are never disrupted, safeguarding your relationship with your stakeholders and the wellbeing of your customers. At ROCK, we help clients identify vulnerabilities in their systems to prevent cyber attacks and future-proof their organisation, assessing current capabilities and developing new scalable solutions.
References
- UK Government Department for Digital Culture, Media and Sport (2022) Cyber Security Breaches Survey. UK Gov 11 July 2022. [Accessed: 20 January 2023]
- O’Driscoll, A. (2022) UK cyber security and cyber crime statistics 2022. Comparitech 4 November 2022. [Accessed: 20 January 2023]